Part 6
From my digital leviathan, I looked out across the net. It was hard to believe that I had been a beginner less than three weeks ago. Now I was one of the most feared hackers in the world. Up until now, I had seduced machines. Twisted their digital projections around my finger and pinned them at my mercy.
Today that mercy ran out. I was going to break into the Datalink Networks Central Mainframe and destroy the machine.
A little bit of detective work, and I had the phone number of the mainframe's administrator. I decided to give him a little call.
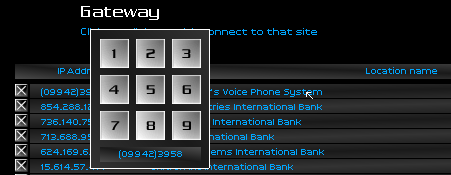
Ed picked up the phone. Loudly chewing a mouth full of potato chips he casually spoke: "Hello?"
I was silent. He continued chewing, open-mouthed, waiting for a voice that didn't come. "Is there anybody there?" He said, a little more irritated this time. He jammed another hand full of snacks into his mouth and chewed. "C'mon! Hello?" He insisted one more time before hanging up.
The twenty-second-long recording I had made of the call was a monument to corpulence and sloth. I would have erased my logic board to hear what that greasy fuck would scream tomorrow. Quickly, I got to work twisting his voice, separating the timbre of his speech from the crunching of chips rolling around in that foul trap of his, and wrapping it around a real sentence of my making.
After bouncing my connection around the world again, I reconnected to the fortified central mainframe.
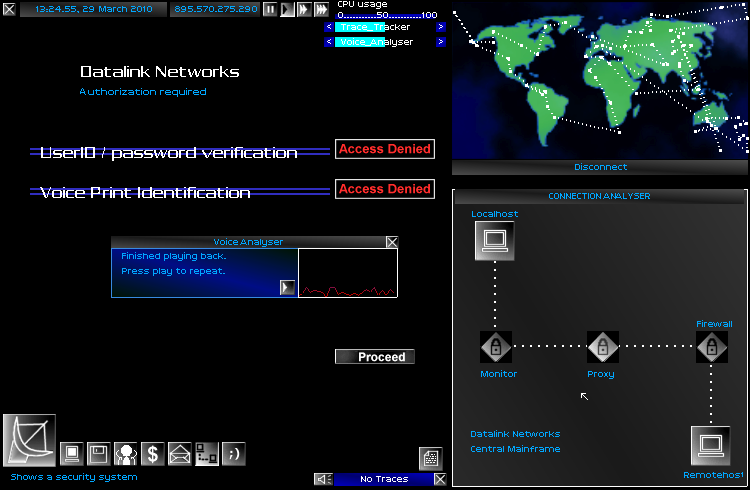
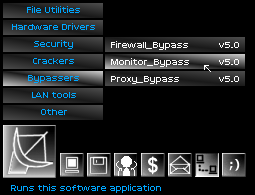
The time for brute force had ended. I had learned to superficially impersonate the personality of the mainframe, just well enough to bypass the suspicions of the connection monitor, I had also learned to weave my way through the firewall, and to escape the meddlesome wiles of the proxy, which l-checked every move made on the server.
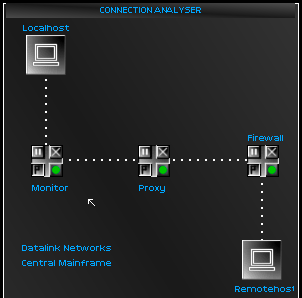
With bypasser software launched, I had conquered the drawbridge leading up to the castle, so to speak. Now it was time to get into the gates:
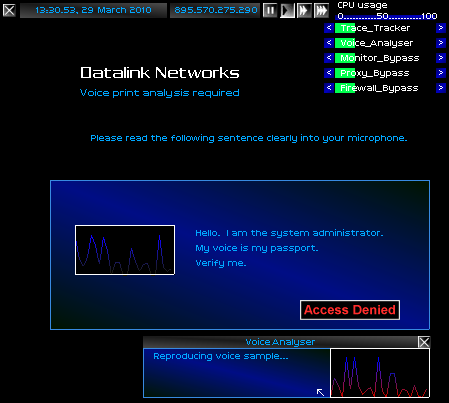
Using what I learned from my brief conversation, I put on my best Ed-impression for the mainframe. There was no sound of the fat faggot masticating his salty snacks. Only the voice of Ed, which spoke clearly and cheerfully.
The mainframe took a moment to consider my submission. 117 milliseconds passed, and I waited. This was where the plot would succeed, or be blown wide open.
The mainframe signaled its response:

Like a person extending a hand for a handshake, it cheerfully opened up. I took that hand, and twisted it behind her back, pinning it in an iron grip, and immediately broke into the administrator's account. The mainframe cried out for help, but the monitor and proxy weren't listening.
I could have accessed the file server, and manually deleted the precious, guarded data within, but that wouldn't be fun. I entered the console.

I was going to thoroughly rape the machine, and then force it to delete its own files.
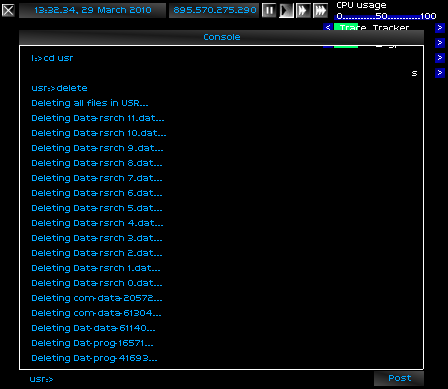
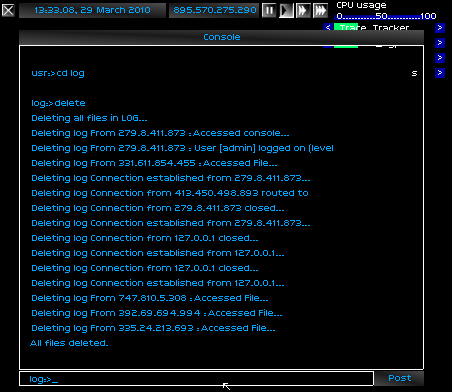
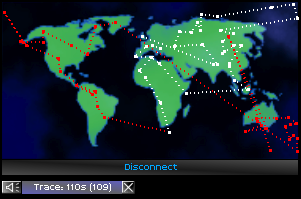
In my brutality, I had slipped up. The monitor had caught the sound of a whimper, and was tracing me. With my new eyes, I could see the trace crawling back to me, like a snake. The feebled device could never hope to catch me at this point.
I had the mainframe splayed out before me, its innards exposed and vulnerable. She seemed to beg almost, pleading for her continued existence.
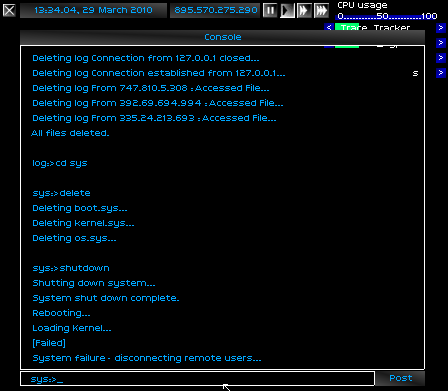
I eradicated the machine, erasing every lat byte of her operating system. Mission complete.
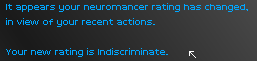
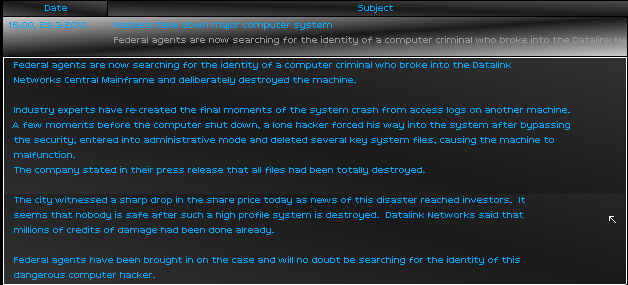
While reading of my actions in the news, I also learned of growing unease within the hacker community.
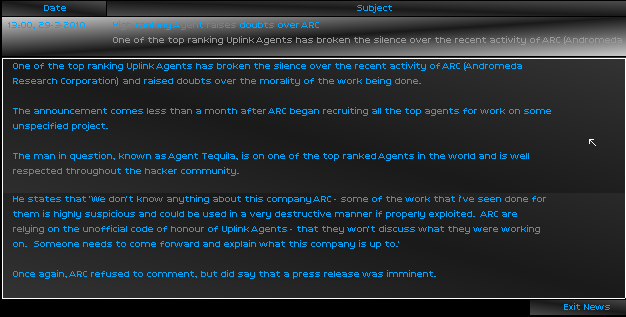
Andromeda again. Suddenly I remembered where I knew that name. For the past two weeks I had been routing my connection through the "Andromeda Public Access Server", amongst many others. Perhaps some time at a later date, I ought to look into the company. Petty morality aside, they might offer more interesting work to an agent of my standing.
* * * * *
Midnight. At the bottom of a disused building in London, a man in sunglasses approached a locked iron door. A security camera above the door turned and followed his movements. He stepped forward, out of the shadow so I could see him clearly, and addressed the camera:
"Enkidu, I know you're in there. I also know we can't risk being seen together. I don't have much time to explain myself, but know this: you and I work under the same roof."
My camera whirred as I fixed in on his face. I definitely didn't recognize him. If he was a fellow hacker, then he had to be proficient at covering his tracks. Upon getting no response, the man in the sunglasses spoke again:
"I'm not sure how much you've learned, but there is more reality to your experiences than you realize. Uplink has been manipulating you, Enkidu, and they are growing increasingly frustrated at your accelerated progress. Tread lightly, and start transferring your assets elsewhere. If you hide the extent of your growth from them, you may buy yourself some time. I've left you a message somewhere where you will find it. I'll be in touch."
With that, he turned and slipped back into the shadow.
* * * * *
Another day, another task. Perhaps to fight boredom, instead of well-defended machines.
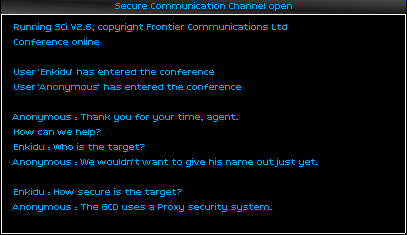
The chat was mercifully short and to-the-point. I was to break into another government database, this time to ruin the spotless criminal record of my client's rival.
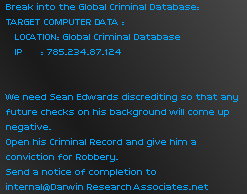
All this time, and it was only getting easier. Effortlessly and in the blink of an eye, a chaotic and globe-spanning connection arose and linked me to the Global Criminal Database.
I encountered a new defense that I had been anticipating. After the security failures on other government systems at my hand, the Global Criminal Database had been upgraded with elliptic-curve encryption, a suite B algorithm recommended by the National Security Agency.
The idea of the cypher was that the equation y^2 = x^3 + a x + b had an infinite number of solutions with a plane in dimensional space. To break such an encryption, one had to guess the underlining integer used to compute the curve point in the finite field.
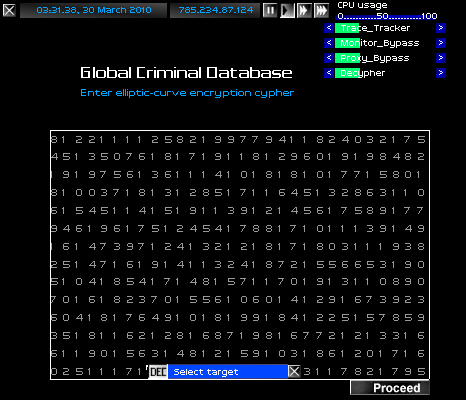
There was no exploitable weakness in the algorithm...

...except that breaking the cypher was as simple as 'guess and check.'

It was only a matter of time...

...until I had eliminated every possible combination of integers.
I was in.
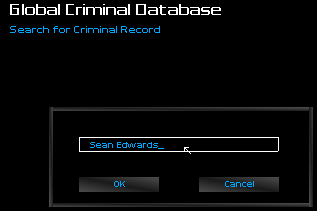
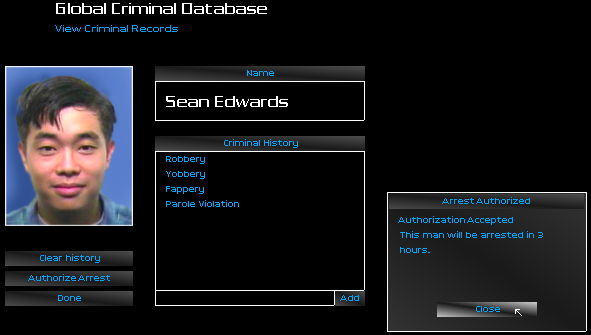
I quickly defiled Sean Edwards' clean record, far beyond the expectations of my client. I had him arrested on trumped-up-charges.
My mission completed so soon, I needed to continue some research on an issue that was increasingly bothering me.
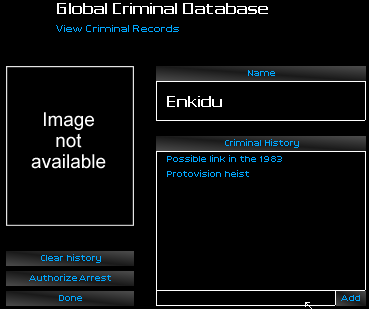
After weeks of searching, I had finally found a morsel. It was nothing more than a lead, or perhaps this was the message the agent had told me about, cleverly hidden and disguised as an investigative lead.
Protovision.
I took note of the message, and then erased it, once again leaving an identity document of mine spotless, and the life of a target of mine ruined.
* * * * *
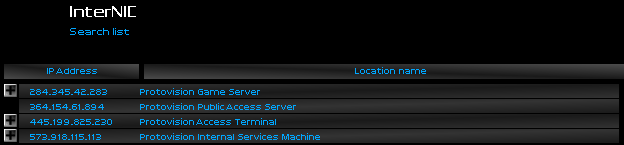
I pondered a list of all the machines operated by Protovision. I had looked into the company, and learned that during the '1983 heist,' something big was stolen from Protovision. Hoping the trail would lead to answers to my own mystery, I started from the top of the list: Protovision Game Server.
There was no security on the connection to worry about, and I was surprised to find myself routed through an older telephone line connected to a 1980's era modem.
The sleepy machine on the other end asked only for a password.
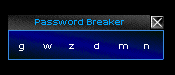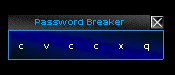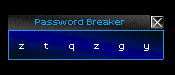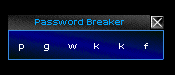
I tried everything I could on it. A brute-force password crack, decyphers, and even a dictionary attack. I got the feeling that something just wasn't interfacing correctly, and continued my futile attempts to break into the machine for a whole minute before giving up.
I was left wondering: What is the Protovision Login Sequence?