Part 3: The Matrix is a lot less kung fu and a lot more tension and panic
The Matrix is a lot less kung fu and a lot more tension and panicTime to find out how well we can survive in the dangerous world of the Matrix. Not well.

Here are the details of the contract we're taking. All we have to do is break into Ron's Repos and turn off the security cameras. It's the height of simplicity! How badly could we fuck this up?

Here we have the Matrix, the main place you'll be spending time in the game. Boy, that's a lot of icons and shit. And did you know some of them change based on the contents of the node you're in? Right now we're in the portal node, the front door of the server. Let's take this one step at a time.
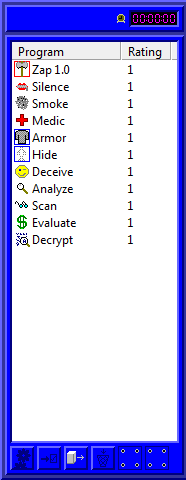
Here are our currently loaded programs. You can double-click them to run them, unless they're a default one, in which case you're turning them off by double-clicking. It's not the smartest idea to do that, unless you're switching from one kind of Attack program to another. Above the menu, there's a clock indicating how long you're spending on the run. One action equates to one second. It doesn't matter how long a run takes, generally, though some things are timed (and yes, you can find contracts with time limits in them). On the bottom is a small number of options for loading or unloading programs from your deck. This takes time.

Here we have the main view of the Matrix, along with a few status bars. Right now, we're looking at our fat orange self, a red Attack program, and an electric fence Gateway program. In the lower left, we have the name of the node we're currently in, a status bar for the node (currently empty because I haven't fucked with anything yet), and an alert status for the server (currently green, which is where it hopefully will stay). In the lower right, we'd see the name and icon of a piece of IC if we had one selected, its status, and its health meter.

Here we have the map screen up at the top, which currently only shows the one node we're in and the one pathway we can see. Different kinds of nodes have different colors and icons on the map screen. In the top left you can (kinda) see the + and - buttons to zoom the map in and out. In the lower left are a bunch of buttons for things we can do; Zzz lets us wait (often used while programs are running), arrow keys to move if for some reason you don't want to use the keyboard, and some fixed buttons for executing certain programs. The middle row is always available, as they show your character screen, cyberdeck screen, and current contract. Below that are some node-specific commands that change based on what kind of node you're in. At the bottom you have a button to disconnect, and a button to bring up Game Options again.
On the lower right, at the top we have our icon's health status. Full green is where it will hopefully stay. The unused space below that is for some software we don't start with, and the empty bar next to the shield icon is where we would see our Shield program's health if we had one. Why it's not also empty space, I don't know. Below that, we have a transfer status bar. When downloading a file, the bar goes to full green and then depletes back to empty as the transfer progresses. Any transfer ended partway through has to be restarted. Then another empty space, and finally status icons for our passive programs (in this case Armor and Hide).
And lastly is the text field, where we get notified of various things.
Since we're here, let's show off our first program: Analyze.

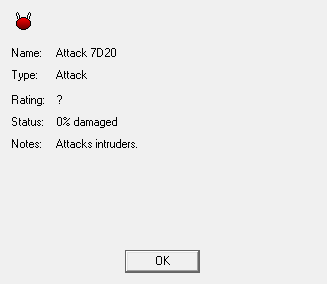
Here we have our Analyze feedback on the Gateway and Attack programs. Because of our low skills and ratings, we can't tell what rating these programs are, but they're usually within 1 of the server's rating (which, recall, is 1).
This also highlights the different types of IC. Gateway is an active IC, or white IC; it sits there and actively looks for icons as they try to leave the node. The Attack program is passive IC, and could be either grey or black IC; it just sits there doing nothing until informed by other IC (in this case, the Gateway) that something is wrong, at which point it springs into action. Most IC at this point will be grey IC, which just attacks our icon until it crashes, which will unceremoniously dump us out of the Matrix. Black IC actually attacks our brain, doing physical damage to us and potentially killing us.
At this point, we're hidden from both programs, but we're going to risk being caught by moving past the gateway and into the next node...
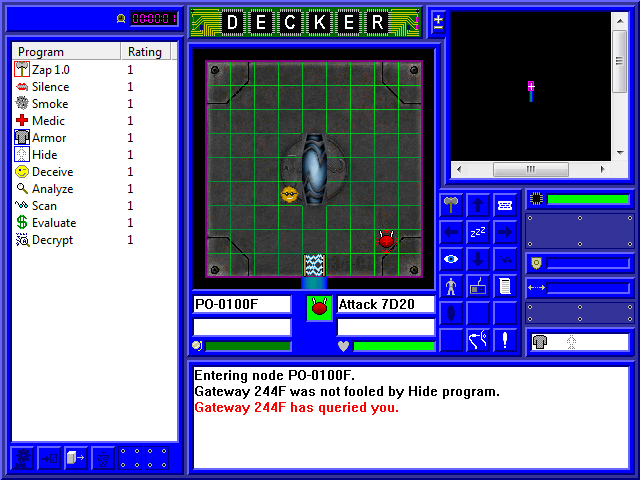
Well, shit! The Gateway managed to beat my Hide program and spot me, and now it wants verification that I'm a legitimate icon (hint: being a decker, I'm not). Fortunately, I have a program that will take of that problem for me: Deceive.

A successful use of Deceive informs the Gateway that I'm totally legit, and I can now pass by it and move on to the next node. It's worth noting, however, that if you don't succeed in Deceiving the Gateway in the portal before the system gets to red alert, your only option is to try to kill the Gateway. While the Attack IC is pounding away at you. And reinforcements are on the way. Needless to say, unless you're a combat monster, all you can really do is jack out and come to terms with what a failure you are.

But that didn't happen here, and we made our way to a Junction node. This is a pretty boring node with nothing in it, though; it just acts as a hallway between more useful nodes. It's worth noting that there's another Gateway IC blocking the way back to where we just came from. Gateway IC always come in pairs like that.

A little traveling later, and we hit a Datastore, a node that holds files on the server. It's a dark blue square thing on the map, and it can have a fairly random amount of IC; sometimes they're completely unguarded, but this one has some guy kind of standing there along with several kind of snake-looking thing. Let's Analyze them!

The first is a Guardian, another active IC. Like the Gateway IC, it will actively look for any icons that are hidden. While the Gateway looked for ones trying to move past it, this Guardian looks for anyone trying to access the node.
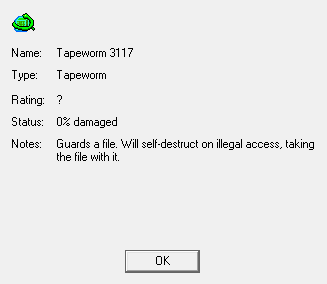
The second is a Tapeworm. Tapeworm IC will encrypt and protect a single file in a datastore. Since there are four on the screen, four files are protected. While the Tapeworm is there and while we remain hidden, we can't tell what kind of file the tapeworm is protecting. Even worse, if we try to tamper with either the tapeworm or the file and fail, the tapeworm will crash and delete the file in the process. If it's a file we're supposed to steal or edit, we can't complete the mission.
There are a couple options for dealing with Tapeworms. The Decrypt program is specifically to crash Tapeworm IC without erasing the file. We could also try an Attack program, but we'd have to kill it in one shot; otherwise, it'll be alerted and crash itself. If you're looking for a file and find Tapeworm, your best shot is to look in every datastore to make sure the contract file isn't unguarded. If it is... welp, good luck!
How do we find out what files are in a datastore, you ask? By using a program, of course! In this case, the Scan program. Scan is to nodes what Analyze is to IC: it'll tell us about the node we're currently in. In a datastore, that means what files are stored here.

Unfortunately, Scan takes times to examine every file, and in the meantime we've been accosted by a blue ball of some sort. Now, when queried by IC, you actually have an extra second to respond. In this case, let's use that second to Analyze what this is.
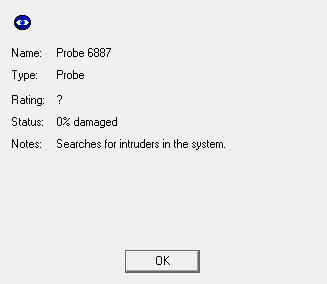
Aha, it's a Probe IC. Probes are like the cops of the server; they walk a beat, looking in every node for hidden icons (i.e. us). They're also really annoying because they produce a lot of messages in the text box. So all we have to do is flash our fake ID at it, and it goes back on patrol.
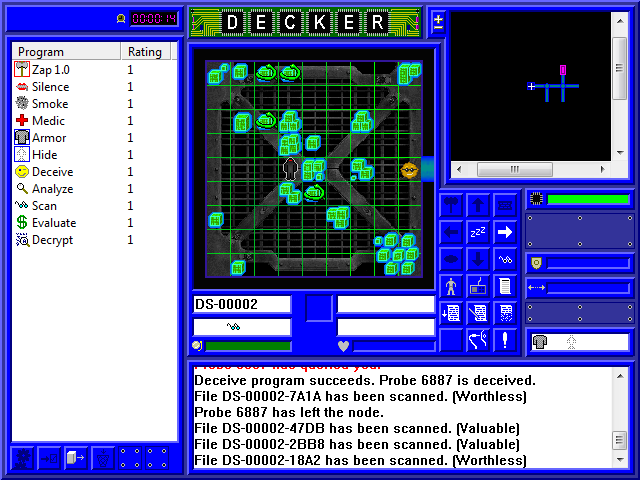
Meanwhile our Scan continues to scan, and while most of the files are worthless, a few are marked Valuable. Valuable files are potentially paydata, and while we haven't actually done our mission yet, we might as well scam a little extra nuyen while we're here. For that, we use our Evaluate program. Evaluate will, uh, evaluate every file marked Valuable to find out how much it's actually worth on the open market.
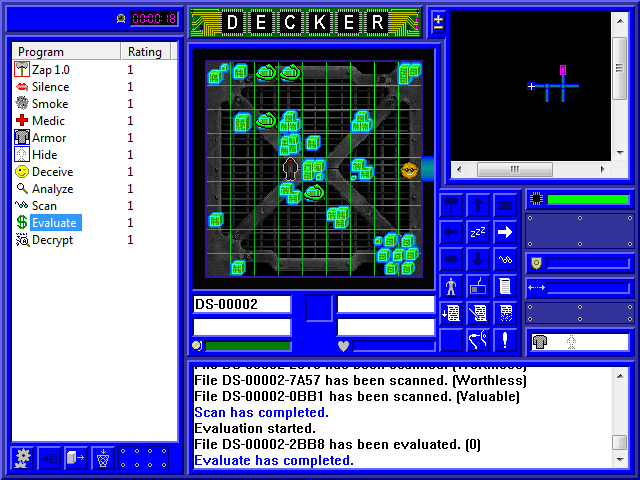
Unfortunately, we only get one result, and that file's worthless. That means the other Valuable files are the ones protected by the Tapeworms, and we can't actually evaluate them until the Tapeworm is dealt with. So we'll just let this stuff go for now.
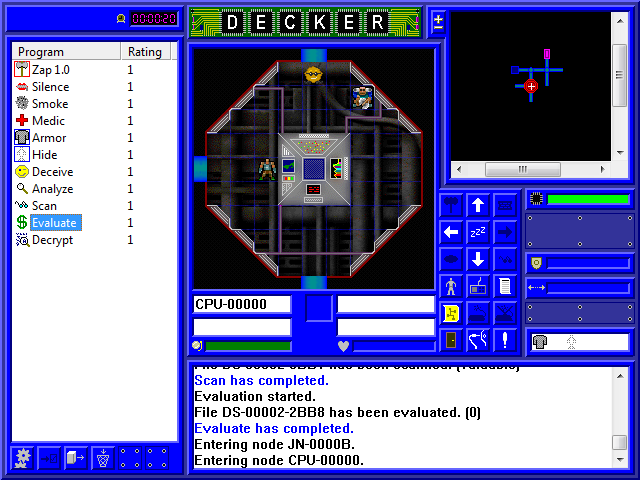
After a little more exploring, what do we find but the CPU! The CPU lets us do a number of useful actions, but it's also usually heavily guarded. In this case, it's got a Guardian and an Attack IC at the ready. In fact...
It's not just an Attack IC, but it's a Brute! Brutes are basically higher rated Attack IC, so we can pretty much assume this is a rating 2 IC. Quite enough to kick our rating 1 ass. That doesn't mean we need to wet ourselves just yet, though. What we want to do right now, with the yellow button we now have available, is get a map of the system. So let's try it out...

Well, fuck! Not only did the Guardian spot us, but it didn't buy our fake ID! Failing with Deceive causes the IC to bump up the system alert by one level, so we're sitting on a yellow alert. And we still have to answer to the Guardian! The last thing we want is a red alert; fortunately, we have a program for that: Silence.

Silence is a status we can put on the node (note the zipped lips icon above the yellow alert indicator) that prevents any IC in the node from raising the alert level. Silence lasts a random amount of time, but if it works we'll get at least one second out of it. (Yes, it can fail to work.) We're going to use that second to flash our fake ID again, and if it fails, the system will stay on yellow alert. Of course, all the IC will go to red alert for having seen me fail, so that Brute will start attacking.

Well, that could hardly have gone worse. Not only did Deceive fail, but the node was only silenced for the one second. At least the Brute missed its first attack. Now, if we don't Silence the node again, the IC will trigger a red alert, and we'll be in trouble. But if we try to escape, that Brute will follow us and keep attacking. So not only do we have to silence the node, but also run our Smoke program. Smoke is another node status; it lets us leave the node and regain our hidden status when we do so.

Luckily, not only do they both work on the first try, but Silence is lasting more than one second AND the Brute only landed one out of three attacks! Now all we have to do is leave the node, and we'll have just minor damage and a yellow alert.
Unluckily, I was still stupid enough to want that area map, so I went back into the CPU to try again.
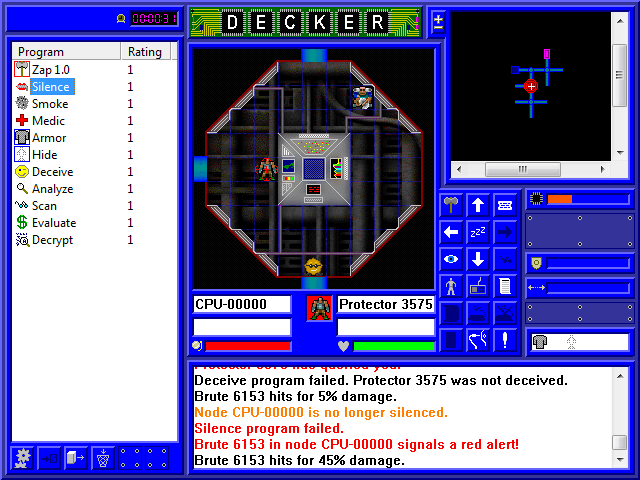
Not only did I fail to hide from the Guardian, I failed to deceive it. And the silence status chose that moment to expire. And the program failed when I tried to re-silence the node. And I got my shit kicked in by the Brute.
So here we are with a red alert, 30% of our health, and an unfinished mission. On the bright side, the alert can't get any worse, so all I need to do is smoke the node and run.
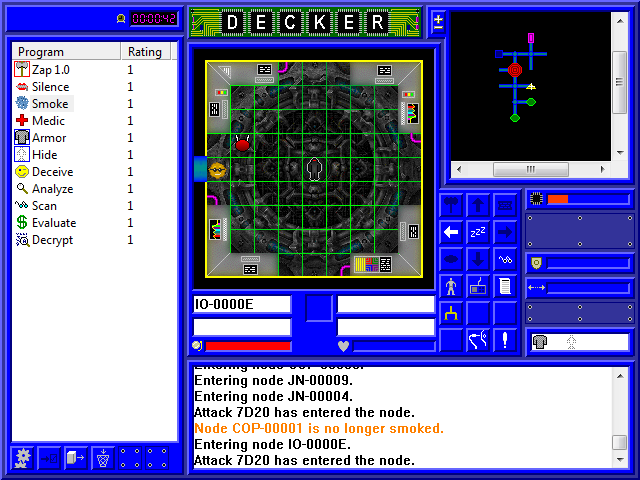
After running around for a while, we make it to our first I/O node, represented on the map by a yellow triangle. I/O nodes can be contract targets (like the security cameras we're looking for), but several also fill a role on the server. Let's see what kind of I/O this is with a quick Scan.

Well, this one handled administrator alarm notifications. You see, once a server hits red alert, a notification is sent to the server admin sitting at a desk somewhere. The admin responds by initiating a server shutdown, which would dump us and fail our mission (if it weren't already completed). It takes a semi-random length of time for the admin to initiate the shutdown, and another semi-random length of time from initiation to actual shutdown. However, since the red alert already happened, shutting off this node is useless; the admin has already been notified.

I take a (relatively) quiet moment during all this to run Medic. Medic is one of a few degrading programs: every time it successfully runs, its rating falls by 1. If it's run while at rating 1, it crashes afterward. To restore the program, you have to load it from your cyberdeck back into memory. This takes time based on the size of the program and the speed of your connection. Since this got me from 30% to 80%, I'm going to call that good enough and leave Medic crashed.

I later find another I/O node, but this isn't the target either. The text box informs us that this node is the entry point for IC. Now you may be wondering why that matters, given that IC is already set up in the system. What isn't obvious is that any IC that crashes (from being attacked or as part of its function) will automatically be reloaded by the system, and they'll come through this node to do it. Shutting off this node will shut off reinforcements, so if you're focused on combat or have a contract that requires you to get some IC out of your way, this is an important node to take out first.
Naturally since we're already at red alert and not planning to fight, this is now useless to us and I leave it alone.
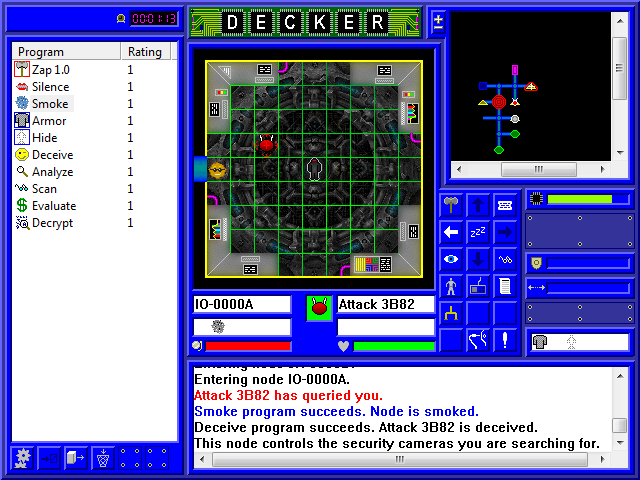
Aha! This is the target node, the security cameras we want. Having found the target node, it becomes highlighted in red on the mini-map. And since, as you can see in the text box, we just successfully deceived that Attack IC, the Guardian IC sitting on the node will also recognize us as legitimate. All we have to do is flip the switch, then unplug ourselves before things somehow get even worse.
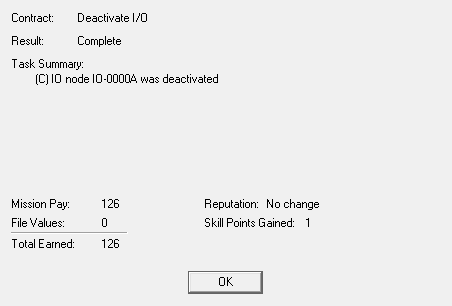
In the end, it wasn't pretty, but we did the job and got our paycheck, plus a skill point. And that's a quarter of our rent right there in one job!
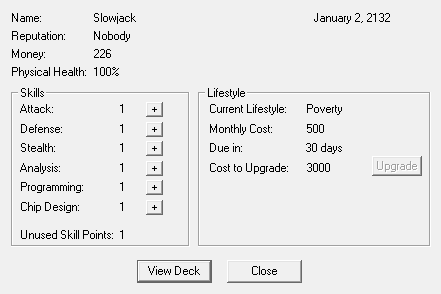
The final thing to note is that, no matter how long or short a Matrix run is, when you jack out or get dumped, a day goes by. So it's now January 2nd, we've got (almost) half our rent money, and we can actually improve a skill! Things are looking up.