Part 2
Those clever bastards. After completing their test scenario, I was now a rated uplink agent. I was also penniless and heavily in debt, to their loans department. They promised me freedom, but now they owned me.

No way out of this mess but forward. To pay off my debt, I needed to whore my services out to the first bidder on the mission postings to take me in.
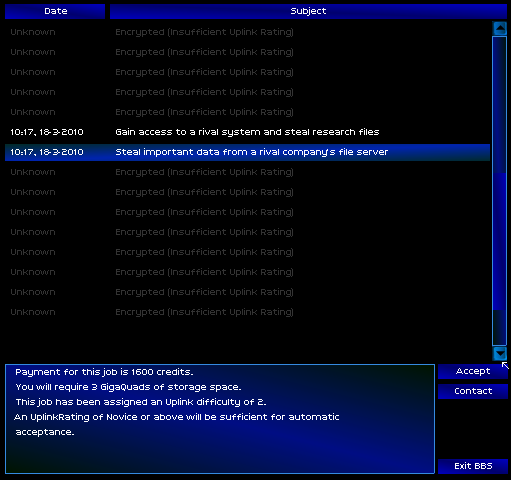
For now, there was nothing available but smash-and-grab jobs. Companies spying on other companies, copying their data for their own uses. The technology industry had become increasingly cutthroat in recent years, to my benefit.
Because so little was known about my qualifications, I needed to chat with a client first, before I accepted their mission.
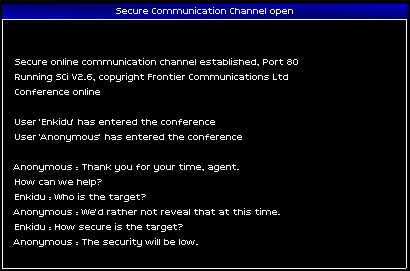
No words were spared. The client was vague, evasive, and obviously uncomfortable with posting this job. Favoring discretion, I held back the other questions I had. "Okay, I'll take the job." I told him, and the chat was immediately closed from the other end.
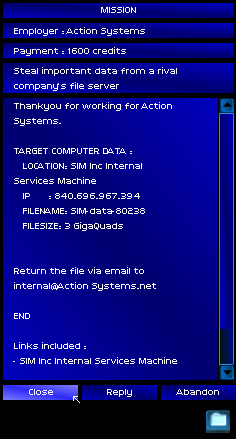
A real client. A real target, the SIM Inc. Internal Services Machine, which would doubtlessly pursue me more aggressively than that mouldering test machine. I would need a tougher connection to trace, starting with more proxies.
The best place to find more servers to bounce a connection through was the InterNIC, an automated internet directory operated and maintained by one of the companies Google had been split into a couple years back.
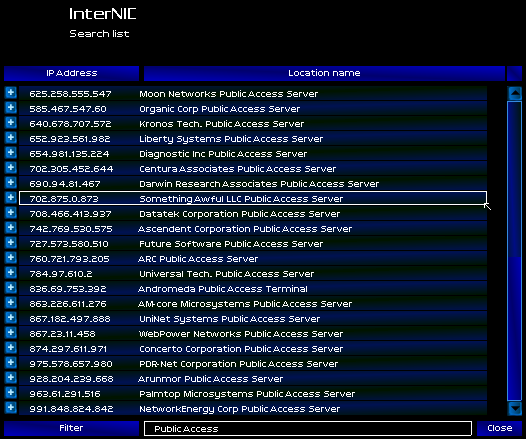
My search results turned up a number of interesting results, but there were so many that I added the first ten to my list of tracked links. Time to roll:
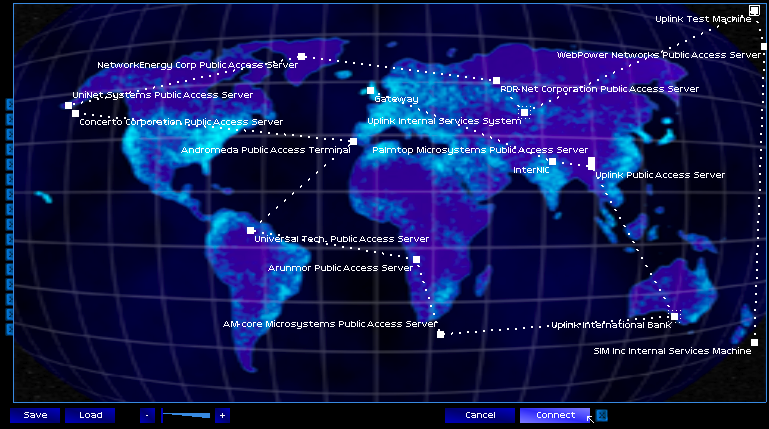
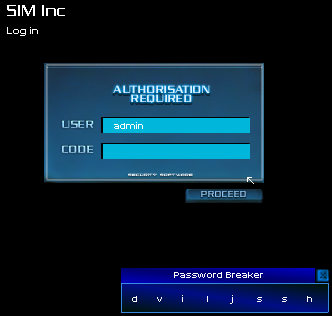
Twenty seconds later, mission complete. The SIM Inc. Internal Services Machine had futilely attempted to trace my connection, but was bounced across the globe from server to another as my password breaker broke into the admin's account.
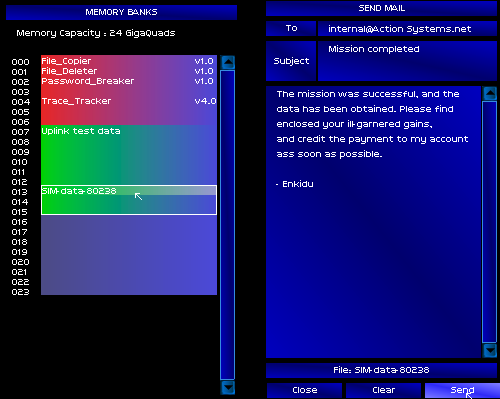
How would the nervous man on the other end of the chat respond to my jab?
Formally. Damn this was easy.
Soon, I was taking on multiple data theft missions, from multiple clients at once.

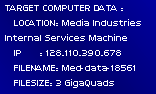
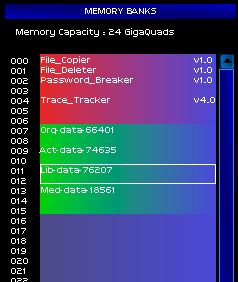
My memory banks swelled with stolen data. Customer records, internal directories, scientific data, experimental computer code...
...and my inbox swelled with congratulations and praise.
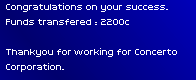
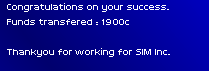
Over the course of an afternoon, I had singlehandedly depleted all the job offers for an agent of my modest rating.
I felt like hot shit. After robbing another database of its valuable cargo, I was exploring the machine out of curiosity when I stumbled upon some bad news:
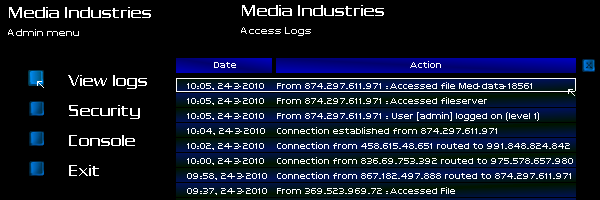
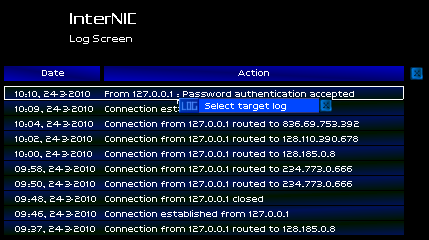
Oh shit. Every machine I had hacked, and every machine I had routed a connection through, kept system logs. My entire afternoon hacking-spree had been logged and noted with cold precision by every machine I had graced.
Though I had foiled all attempts at active tracing by closing connections, I couldn't stop someone from looking at the logs, and tracing it from server to server at their leisure. Every job I had taken, every machine I had hacked, left an international trail leading back to me.
I would have to cut them off somehow. It wasn't cheap, but I found a solution.
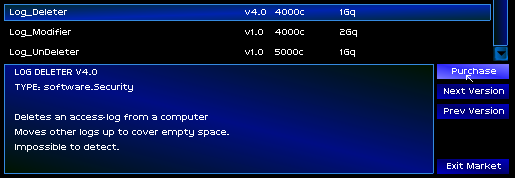
Every connection I had made that afternoon had been routed through the InterNIC. If I could gain access to the machine, I could erase all the incriminating logs and the trail would be cut off.
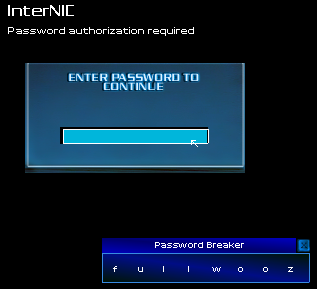
Now I was scott-free. Having covered my tracks, nobody would ever kn-
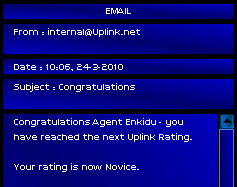
How did they know? Thank god the invisible man breathing down my neck is on my side. Uplink would have let me walk right into that trap, had it not been for my chance discovery.
But at least I wasn't a bottom-feeder any more. I logged on to the bank, to tally my gains of the afternoon. The log-deleter program was top-of-the-line, but it had cost a pretty penny. After that, a vast majority of my remaining money went to the repayment of my loan.
Once more, I was pretty much broke, and still in need of money despite the afternoon's work. My increase in rank opened up new, higher-paying opportunities.
I logged onto the chat once more. The anonymous client on the other end greeted me. "How much are you offering for the job?" I typed.
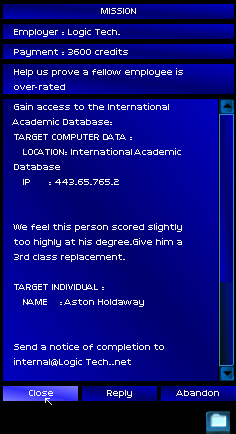
"Thirty six hundred credits upon completion, no advances."
"Who's the target?" I asked. This client seemed to be more open than the first one.
"You wouldn't know him, but he's a complete dick."
"I don't understand." I replied, intrigued. "What am I hacking?"
"This aint no mom-and-pop company server, Enkidu." He LOLed. "Your target is the International Academic Database!"